| Citation: | JIAO Zhipeng, CHEN Hua, FENG Jingyi, KUANG Xiaoyun, YANG Yiwei, LI Haoyuan, FAN Limin. A Combined Countermeasure Against Side-Channel and Fault Attack with Threshold Implementation Technique[J]. Chinese Journal of Electronics, 2023, 32(2): 199-208. DOI: 10.23919/cje.2021.00.089 |
As we know, a mathematically secure cryptographic algorithm does not mean it is secure in practice. A lot of implementation attacks have been proposed, among which side-channel attack (SCA) and fault attack (FA) are two main kinds of physical attacks against cryptographic implementations. SCA seeks the information leakage which is correlated with some sensitive information such as the secret key. By exploring the dependence between the information leakage and the sensitive information, the attacker can recover the secret. One of the most popular side-channel information leakage is the power consumption from the cryptographic implementations. In 1999, Kocher et al. proposed differential power attack (DPA) firstly [1]. Since then, various kinds of power attacks have been presented including correlation power attack (CPA) [2], template attack (TA) [3] and so on. Meanwhile, how to efficiently resist the attack is also investigated. Masking technique [4] is one of the most popular countermeasures against SCA from the view of algorithmic level, which includes Boolean masking and multiplication masking. In a Boolean masking scheme, random values are applied exclusive-or operation with some intermediate values during cryptographic operations, which can hide the possible dependence between the side-channel information leakage from intermediate operations and sensitive data. Among Boolean masking schemes, threshold implementation (TI) technique [5] has caused much research attention in recent years. Besides the SCA, the first FA against cryptographic implementation was given by Boneh et al. in EUROCRYPT’97 [6]. After that, FAs against various kinds of cipher schemes were proposed including DES [7], AES [8], DBlock [9], and so on. Infection [10] is one of the most popular countermeasures to resist FA. It requires the redundant computations besides the original ones in the cipher algorithm. The infective countermeasure is realized by scrambling the data paths of the original and redundant computations. The well-designed infection can make the final faulty ciphertext independent from the secret key.
The countermeasures mentioned above only consider single SCA or FA. One of the main drawbacks is, they are easily vulnerable to another attack or combined attack. To defend both SCA and FA, a popular method is to combine the SCA-resistant techniques with the FA-resistant ones. For instance, Private Circuits II is constructed based on Private Circuit I together with the FA-resistant encoding gadget [11], however, it cannot guarantee the security under the glitch environment. In CRYPTO 2016, a combined countermeasure called ParTI was presented which combines the concept of TI with the concurrent error detection techniques [12]. Recently, many designers adopt multi-party computation (MPC) protocols and infective techniques in the combined countermeasures. CAPA takes MPC protocol SPDZ, along with corresponding shared MAC tags [13], it is of formal security, but its resource consumption is too much. M&M achieves an efficient countermeasure with TI and multiplication-based MAC operation [14]. There are also countermeasures that adopt a single technique to resist both SCA and FA. The countermeasure in CT-RSA 2017 achieves the comprehensive resistance with the encoding technique [15]. The one in CHES 2018 takes the MPC based on polynomial to disable SCA and detect the fault injection [16]. To sum up, although some of the protection schemes introduced above have high safety, they have a common shortcoming, namely high resource consumption. In view of this phenomenon, this paper proposes a comprehensive protection scheme with less resource consumption.
Our contributions In this paper, we present a combined countermeasure scheme which can resist both SCA and FA. Different from the methods mentioned before, we combine the TI technique and exchange-based infection scheme to resist the two attacks. The details are as follows.
1) A combined countermeasure scheme based on TI technique and exchange-based infection is proposed. TI can not only provide protection against power attack, but also can be combined with exchange-based infection to enhance its resistance to FA. The advantage of the proposed countermeasure is the simple structure, which is very friendly for hardware implementation.
2) The security of the scheme is analyzed systematically. The proposed combined countermeasure has at least the same level of SCA-security as a plain d-order TI without FA countermeasures. The scrambled implementation based on duplication structure together with TI provide protection against FA. The scrambled implementation confuses the fault propagation path. TI realizes the segmentation of the original fault value, and the non-complete property of TI makes the information of the original fault value difficult to be obtained by the attacker.
3) Finally, we give a case design for the lightweight cryptographic algorithm LED which can achieve the 1-order SCA security and resist the differential fault attack. Besides, we verified its low overhead and resistance against SCA and FA on SAKURA-X FPGA evaluation board.
TI is a popular countermeasure against SCA [5]. It is constructed based on secret sharing and multi-party computation protocols. To resist the
Input encoding splits the input
The key of TI lies in the function coding. The number of shares required in TI is jointly determined by the order of SCA and the algebraic degree of the cipher function. Reference [18] has proved that for the functions with algebraic degree of
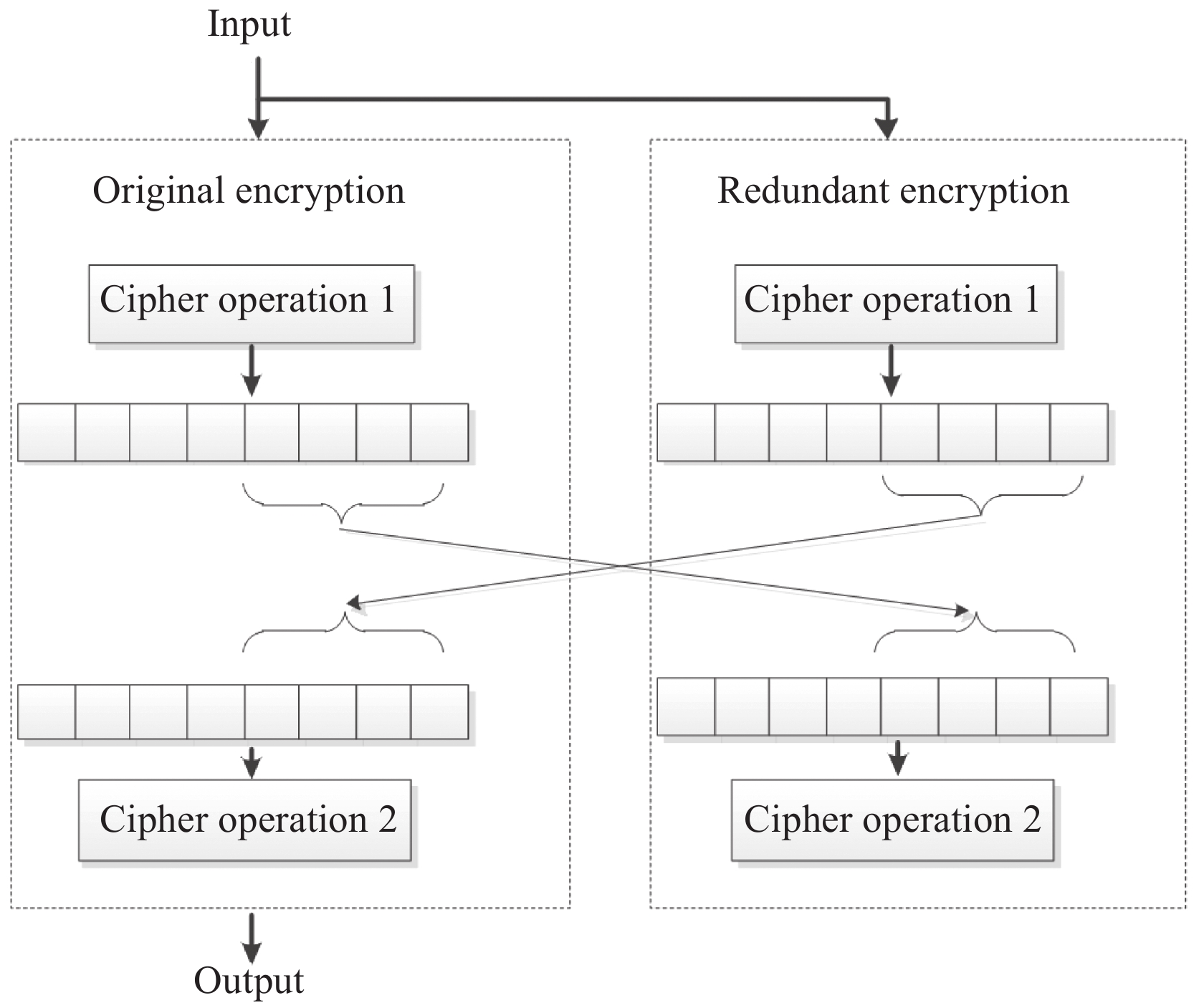
The exchange scheme proposed by Joye et al. is a countermeasure against FA [10]. The main idea is duplicating the cipher implementation, exchanging the original and redundant intermediates during the encryption, and outputting the original encryption result as the final ciphertext. Take the encryption process “cipher operation 1,” and “cipher operation 2” as an example and Fig.1 illustrates it. The exchange is performed between the last 4 bits of the intermediates. Concerning the fault injection on the last 2 bits of the input of the original “cipher operation 1,” after the exchange operation, the faulty bits are swapped with the correct ones. The output ciphertext will not yield the expected fault. The countermeasure can resist FA in a certain extent. However, when the fault is injected in some other part of the input, the output faulty bits remain unchanged. Since no randomness has been introduced to the faulty output, it is still possible to perform the attack [19]. In the following part, we will show how the combination with TI can strengthen the resistance of the exchange scheme against the FA.
Our design aims to resist both the SCA and FA. The basic idea is the combination of TI and a special kind of infection scheme. The infection scheme provides the protection on the FA. When a fault is injected, the ciphertext is still outputted, but it has become a random value which can not provide the useful information for the attacker. TI mainly plays the role to resist the power attack. Besides, it also strengthens the resistance against the FA which will be illustrated as follows.
The infection scheme originates from the work of M. Joye in 2007 [10]. In the work, the AES hardware implementation is duplicated and the state bytes are scrambled between the two executions. Such methodology can ensure that a fault on one data path will likely result in a fault on the other data path. So the attacker has difficulty to acquire some knowledge on the fault propagation to succeed in recovering information on the secret key. However, the problem of this methodology is, no randomness is induced into the implementation procedure. So once the attacker knows the fault propagation path, he can also recover the secret key with some more efforts. Our methodology also duplicates the implementation of the cipher, and each path of the cipher is implemented with TI technique. Different from [10], one share or more shares of the state bytes are scrambled between the two executions. By this means, randomness used in TI also helps to confuse the fault propagation. In order to generate the correct ciphertext with no fault injection, the same shared way and random numbers are used in the two data paths.
Next we take a target function
Besides, there is another redundant TI implementation same as
Let
For a multi-output Boolean function
1) Attack model
SCA model The first model we consider is the d-order probing attacks [17]. In this model, the adversary can observe at most
The second model considers the attacker has the ability to collect power supply signal. He can obtain the power consumption of the whole encryption procedure. By analyzing the dependence of the power consumption on the encrypted data, he can recover the secret data. A
FA model In this paper, we mainly consider the most popular fault attack, i.e., Differential fault attack (DFA) [7], [8]. It is based on the concrete faulty output value. Under such attack, both correct encryption execution and wrong execution are needed. By exploring the statistical correlation between the faulty values and the correct ones, the attacker can recover the secret information.
2) SCA evaluation
In our scheme, both the original encryption and the redundant encryption are implemented with TI technique. According to the security property of TI, the two encryption path implemented with the
Next we consider the resistance ability of the exchange operation. Generally, the hardware logic of exchange operation is very simple. Hence, the power leakage is hard to be utilized by the attacker. Here we consider the worst case, in which the power consumption of exchanged
3) FA evaluation
Here we will illustrate the resistance against DFA. The protection against the DFA is derived from both the scrambled implementation based on duplication structure and TI. As described in [10], the scrambled way helps to confuse the fault propagation path. But it is not enough. The following fault analysis on the countermeasure shows that, once the attacker knows the scrambled way, he can also deduce the fault propagation path and then recover secret key. The reason why the attacks can work is that no randomness is induced in the countermeasure. Our countermeasure can overcome the weakness because randomness is induced in the TI, which can also help to confuse the fault value. Moreover, the information of the fault value is also spitted by the shared structure. The non-complete property of TI ensures the whole information of the fault value cannot be obtained by the attacker.
As we know, the implementation of the last round is the most difficult to defend DFA because of the worst diffusion effect when faults are injected in the last-round encryption. So we focus on illustrating the protection effect of last round. Without loss of generality, here we focus on the last TI-target function where the ciphertext will be outputted after the output of function is Xored the round key, which is illustrated by Fig.3.
Denote
When a fault is injected into some intermediate round, after the propagation of the fault, the corresponding last-round intermediate values would change into other new values. We denote the new values by
Case 1 Only one of
As we know,
Case 2
If
From the above security illustration, we can see that, in most cases the scheme is secure against DFA with the help of swapping operation and the TI scheme. However, it can not ensure a perfect protection with probability 1. Some cases will still happen when a fault is induced into low-round encryption and the swapping operation does not change the fault propagation path. The probability of such cases can be effectively reduced by the random swapping operation because the attacker can not get the same ciphertext when the injection condition remains unchanged. Moreover, some penalty functions can also be added to the last-round encryption to further improve the case. In the following countermeasure design of LED, we will design a penalty function with a S-box function and its inverse function. For the case that S-box and inverse S-box are not implemented simultaneously, the Feistel structure with S-box as nonlinear component can be used to extend it.
In this paper, we mainly consider the most popular fault attack-DFA, which utilizes the concrete faulty values of ciphertext to launch the attack. For other faulty value-based attacks such as algebraic fault attack [20], our countermeasure has the similar resistance ability because the ciphertexts are randomized by the infective and TI scheme. However, for those FAs which do not care the concrete faulty ciphertexts, our countermeasure maybe not be applicable. Take the statistical infective fault attack as an example [21], it has been shown neither TI [22] nor infective scheme can resist such attack [21], so our scheme can not resist this attack. More protection requirements mean more resource consumption. In a resource-constrained environment, it is a reasonable strategy to mainly consider the protection for DFA, which is one of the most common and powerful FA methods.
LED is a lightweight block cipher proposed in
LED-64 adopts SPN structure. The whole encryption contains round key addition (AddRoundKey) and STEP operation. The intermediate state is a
AddConstants respectively adds
There is no key schedule for LED-
As introduced in Section III.1, the whole implementation structure of LED-
The swapping way of two paths for each encryption is different. The random numbers which control the exchanged way is generated before each encryption starts. In order to save random numbers, the exchanged way for each round remains the same once the random number is generated at the beginning. Because the security target is
AddRoundKey & AddConstants The round key and constants are only added into one share of intermediate state, which can also ensure the output uniformity and 1-order non-complement property.
ShiftRows The shift operation is respectively applied on each share component. Because the hardware logic is very simple and can be implemented by changing the connecting way, it is omitted in Fig.4.
SubCells LED-64 uses the same 16 4×4 S-boxes of PRESENT. In order to obtain secure TI implementation of S-box with low cost, we adopt the same decomposition way of S-box and TI implementation way as [24]. The decomposition way is as follows:
| S(⋅)=F(G(⋅)).G(x,y,z,w)=(a,b,c,d),a=y+z+w,b=1+y+z,c=1+x+z+yw+zw,d=1+w+xy+xz+yz.F(x,y,z,w)=(a,b,c,d),a=y+z+w+xw,b=x+zw,c=y+z+xw,d=z+yw. |
where
| Gi(xi+1,yi+1,zi+1,wi+1,xi+2,yi+2,zi+2,wi+2)=(ai,bi,ci,di),ai=yi+1⊕zi+1⊕wi+1,bi=1⊕yi+1⊕zi+1,ci=(yi+1wi+1⊕yi+1wi+2⊕yi+2wi+1)⊕zi+1⊕(zi+1wi+1⊕zi+1wi+2⊕zi+2wi+1)⊕1⊕xi+1,di=1⊕wi+1⊕(xi+1yi+1⊕xi+1yi+2⊕xi+2yi+1)⊕(xi+1zi+1⊕xi+1zi+2⊕xi+2zi+1)⊕(yi+1zi+1⊕yi+1zi+2⊕yi+2zi+1).Fi(xi+1,yi+1,zi+1,wi+1,xi+2,yi+2,zi+2,wi+2)=(ai,bi,ci,di),ai=yi+1⊕zi+1⊕wi+1⊕(xi+1wi+1⊕xi+1wi+2⊕xi+2wi+1),bi=xi+1⊕(zi+1wi+1⊕zi+1wi+2⊕zi+2wi+1),ci=yi+1⊕zi+1⊕(xi+1wi+1⊕xi+1wi+2⊕xi+2wi+1),di=zi+1⊕(yi+1wi+1⊕yi+1wi+2⊕yi+2wi+1). |
The index
MixColumnsSerial The column mixture operation is respectively applied on each share component.
Besides the normal encryption, in order to further strengthen the FA resistance for last-round encryption, we add the inverse function
| F−1(x,y,z,w)=(a,b,c,d),a=y⊕z⊕xy⊕xz⊕xw⊕yz⊕zw,b=z⊕w⊕xy⊕xw⊕yz⊕zw,c=z⊕w⊕xy⊕xz⊕yz,d=x⊕z.G−1(x,y,z,w)=(a,b,c,d),a=x⊕w⊕yz,b=1⊕z⊕w⊕xy⊕yz,c=y⊕z⊕w⊕xy⊕yz,d=1⊕x⊕y. |
After the normal encryption, each path will execute
The TI designs of
The random number overhead of the countermeasure contains two parts: the ones required for threshold implementation and the ones needed for the share exchange. The 1-order TI of LED contains 3 shares and 16 S-boxes which are parallelly implemented, so it requires
In LED implementation based on the countermeasure prototype, the encryption requires 64 clock cycles, which is the same as that required in a single SCA countermeasure. As for the improved implementation, it requires four additional clock cycles to complete the encryption, which has little impact on the throughput.
In terms of the hardware overhead of protection, the redundant encryption doubles the circuit area. The share exchange operation between
| Area(kGE) | Latency(clock cycle) | |
| States, keys and constants storage | 4.32 | 0 |
| MixColumns | 3.08 | 0 |
| SubCells | 8.19 | 2 |
| Others | 2.88 | 0 |
| In total | 18.47 | 64 |
In order to compare our FA-SCA resistant countermeasure with the existing ones, we focus on the 1st-order implementations and list their area overheads. To minimize the effects of different synthesis libraries and different cipher algorithms in area, we refer to [14] and use the overhead factor to make the comparison. The overhead factor is the ratio of the FA-SCA countermeasure overhead to the SCA-only countermeasure overhead.
As shown in Table 2 [12]–[14], [25]–[28], our countermeasure has the minimum overhead factor. It is a compact countermeasure to resist both SCA and FA.
To evaluate the resistance of our countermeasure against SCA, we implement the protected LED encryption on Xilinx Kintex-7 FPGA of SAKURA-X board. To avoid the optimizations in the synthesis step break the non-completeness of the countermeasure, we disable the optimization option and keep hierarchy of the design. In the experiment, we make encryption with a slow clock rate (3 MHz) and sample the power traces at a rate of 500 MS/s. Then we perform SCA evaluation with the test vector leakage assessment (TVLA) technology [29]. The assessment takes the
To show the effectiveness of the countermeasure, we first disable the PRNG of the implementation and make assessment on the unprotected LED. Here, the power traces are collected within the first 2 rounds’ encryption, which takes 4 clock cycles. After 2500 times encryptions in each group, Fig.5 summarizes the 1st/2nd/3rd-order
In this section, we focus on the DFA-like attacks that rely on the concrete faulty ciphertexts, and work out how the protected LED can randomize the output.
To achieve this goal, we simulate the repetitive fault injections in the protected LED, and make a statistic analysis on faulty ciphertexts. To be specific,
1) Encrypt the same plaintext for
2) Select a target intermediate share and a fault value. In each encryption, introduce the fault value into the target intermediate share through Xor operation, in order to simulate the repetitive injections with the same fault.
3) Compute the appearance frequency of each faulty ciphertext value in nibble. Then show the randomness of faulty ciphertexts in terms of entropy.
The evaluation focus on the improved LED implementation which adopts 4 extra non-linear operations
| Injection target | Entropy of 16 ciphertext nibbles |
| Input of the last round F (5 exchanges) | 3.878, 3.789, 3.870, 3.857, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0 |
| Input of the last round G (6 exchanges) | 3.951, 3.950, 3.969, 3.962, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0 |
| Input of the penultimate round F (7 exchanges) | 3.992, 3.994, 3.993, 3.994, 3.993, 3.993, 3.993, 3.990, 3.995, 3.992, 3.993, 3.993, 3.993, 3.994, 3.995, 3.992 |
| Input of the penultimate round G (8 exchanges) | 3.999, 3.998, 3.998, 3.998, 3.998, 3.998, 3.998, 3.998, 3.999, 3.998, 3.999, 3.999, 3.998, 3.998, 3.999, 3.998 |
In this paper, we propose a countermeasure which combines TI and Joye exchange scheme. TI technique ensures it is provable secure against SCA. Joye exchange scheme was originally proposed to resist the FA by changing the executing path. However, if the exchanging way is determined, the attack can still guess the fault propagation path and break the countermeasure with some more efforts. Our scheme can strengthen the fault attack ability by exchanging the encryption components in a random way which increase the guess difficulty for the attacker. Moreover, TI diffuses the injected fault into some share components. The incomplete property ensures the original injected fault is independent from the final fault value. Therefore, TI also helps to increase the resistance against fault attack.
Based on the scheme, we also design a case countermeasure for the lightweight block cipher LED-64. According to the S-box property, we design a 3-share based scheme and each time only one share is exchanged. We also implement it in the FPGA evaluation board SAKURA-X. The hardware evaluation shows it has low cost compared with other methods. Besides, we apply the TVLA method to evaluate the resistance against SCA and can not find the 1-order sensitive information leakage. For the FA, the entropy of faulty ciphertext is near to 4, so the faulty ciphertext can be seen as random which means it is secure against faulty value based attack.
| [1] |
P. Kocher, J. Jaffe, and B. Jun, “Differential power analysis,” in Proceedings of 19th Annual International Cryptology Conference, Santa Barbara, CA, USA, pp.388–397, 1999.
|
| [2] |
E. Brier, C. Clavier, and F. Olivier, “Correlation power analysis with a leakage model,” in Proceedings of International Workshop on Cryptographic Hardware and Embedded Systems, Cambridge, MA, USA, pp.16–29, 2004.
|
| [3] |
Suresh Chari, Josyula R. Rao, and Pankaj Rohatgi, “Template attacks,” in Proceedings of International Workshop on Cryptographic Hardware and Embedded Systems, Redwood Shores, CA, USA, pp.13–28, 2002.
|
| [4] |
L. Goubin and J. Patarin, “DES and differential power analysis the ‘duplication’ method,” in Proceedings of International Workshop on Cryptographic Hardware and Embedded Systems, Worcester, MA, USA, pp.158–172, 1999.
|
| [5] |
Svetla Nikova, Christian Rechberger, and Vincent Rijmen, “Threshold implementations against side-channel attacks and glitches,” in Proceedings of International Conference on Information and Communications Security, Raleigh, NC, USA, pp.529–545, 2006.
|
| [6] |
D. Boneh, R. DeMillo, and R. Lipton, “On the importance of checking cryptographic protocols for faults,” in Proceedings of International Conference on the Theory and Application of Cryptographic Techniques, Konstanz, Germany, pp.37–51, 1997.
|
| [7] |
Eli Biham and Adi Shamir, “Differential fault analysis of secret key cryptosystems,” in Proceedings of 17th Annual International Cryptology Conference, Santa Barbara, California, USA, pp.513–525, 1997.
|
| [8] |
Pierre Dusart, Gilles Letourneux, and Olivier Vivolo, “Differential fault analysis on A.E.S,” in Proceedings of First International Conference on Applied Cryptography and Network Security, Kunming, China, pp.293–306, 2003.
|
| [9] |
Jingyi Feng, Hua Chen, Si Gao, et al., “Fault analysis on a new block cipher dblock with at most two fault injections,” Chinese Journal of Electronics, vol.27, no.6, pp.1277–1282, 2018. DOI: 10.1049/cje.2018.09.003
|
| [10] |
M. Joye, P. Manet, and J. B. Rigaud, “Strengthening hardware AES implementations against fault attacks,” IET Information Security, vol.1, no.3, pp.106–110, 2007. DOI: 10.1049/iet-ifs:20060163
|
| [11] |
Yuval Ishai, Manoj Prabhakaran, Amit Sahai, et al., “Private circuits Ⅱ: Keeping secrets in tamperable circuits,” in Proceedings of 25th International Conference on the Theory and Applications of Cryptographic Techniques, St. Petersburg, Russia, pp.308–327, 2006.
|
| [12] |
T. Schneider, A. Moradi, and T. Güneysu, “ParTI – towards combined hardware countermeasures against side-channeland fault-injection attacks,” in Proceedings of 36th Annual International Cryptology Conference, Santa Barbara, USA, pp.302–332, 2016.
|
| [13] |
Oscar Reparaz, Lauren De Meyer, Begül Bilgin, et al., “CAPA: The spirit of beaver against physical attacks,” in Proceedings of 38th Annual International Cryptology Conference 2018, Santa Barbara, CA, USA, pp.121–151, 2018.
|
| [14] |
L. De Meyer, V. Arribas, S. Nikova, et al., “M & M: Masks and macs against physical attacks,” IACR Transactions on Cryptographic Hardware and Embedded Systems, vol.2019, no.1, pp.25–50, 2019. DOI: 10.13154/tches.v2019.i1.25-50
|
| [15] |
Jakub Breier and Xiaolu Hou, “Feeding two cats with one bowl: On designing a fault and side-channel resistant software encoding scheme,” in Proceedings of thehe Cryptographers’ Track at the RSA Conference 2017, San Francisco, CA, USA, pp.77–94, 2017.
|
| [16] |
O. Seker, A. Fernandez-Rubio, T. Eisenbarth, et al., “Extending glitch- free multiparty protocols to resist fault injection attacks,” IACR Transactions on Cryptographic Hardware and Embedded Systems, vol.2018, no.3, pp.394–430, 2018. DOI: 10.13154/tches.v2018.i3.394-430
|
| [17] |
Yuval Ishai, Amit Sahai, and David Wagner, “Private circuits: Securing hardware against probing attacks,” in Proceedings of 23rd Annual International Cryptology Conference, Santa Barbara, California, USA, pp.463–481, 2003.
|
| [18] |
Begül Bilgin, “Threshold implementations: As countermeasure against higher-order differential power analysis,” Ph.D. Thesis, University of KU Leuven at Heverlee, Belgium, University of Twente at Enschede, Netherlands, 2015
|
| [19] |
V. Lomne, T. Roche, and A. Thillard, “On the need of randomness in fault attack countermeasures-application to AES,” in Proceedings of the 2012 Workshop on Fault Diagnosis and Tolerance in Cryptography, Leuven, Belgium, pp.85–94, 2012.
|
| [20] |
N. T. Courtois, D. Ware, and K. M. Jackson, “Fault-Algebraic Attacks on Inner Rounds of DES,” in Proceedings of the eSmart 2010 European Smart Card Security Conference, Riviera, French, pp.22–24, 2010.
|
| [21] |
C. Dobraunig, M. Eichlseder, T. Korak, et al., “SIFA: exploiting ineffective fault inductions on symmetric cryptography,” IACR Transactions on Cryptographic Hardware and Embedded Systems, vol.2018, no.3, pp.547–572, 2018.
|
| [22] |
C. Dobraunig, M. Eichlseder, H. Gross, et al., “Statistical ineffective fault attacks on masked AES with fault countermeasures,” in Proceedings of International Conference on the Theory and Application of Cryptology and Information Security, Brisbane, QLD, Australia, pp.315–342, 2018.
|
| [23] |
Jian Guo, Thomas Peyrin, Axel Poschmann, et al., “The LED block cipher,” in Proceedings of International Workshop on Cryptographic Hardware and Embedded Systems, Nara, Japan, pp.326–341, 2011.
|
| [24] |
A. Poschmann, A. Moradi, K. Khoo, et al., “Side-channel resistant crypto for less than 2,300 GE,” Journal of Cryptology, vol.24, no.2, pp.322–345, 2011.
|
| [25] |
Faraday Technology Corporation, “Faraday FSA0A C 0.18 μm ASIC,” Available at: http://www.faraday-tech.com, 2004.
|
| [26] |
T. de Cnudde and S. Nikova, “More efficient private circuits II through threshold implementations,” in Proceedings of 2016 Workshop on Fault Diagnosis and Tolerance in Cryptography, Santa Barbara, CA, USA, pp.114–124, 2016.
|
| [27] |
NANGATE, “The NanGate 45 nm Open Cell Library,” Available at: http://www.nangate.com, 2008.
|
| [28] |
Virtual Silicon Inc, “0.18 μm VIP Standard cell library tape out ready, partnumber: UMCL18G212T3, process: UMC logic 0.18 μm generic Ⅱ technology: 0.18 μm,” 2004.
|
| [29] |
Goodwill Gilbert, Jun Benjamin, Jaffe Josh, et al., “A testing methodology for side-channel resistance validation,” NIST Non-invasive Attack Testing Workshop, Nara, Japan, pp.115–136, 2011.
|
| [30] |
Tobias Schneider and Amir Moradi, “Leakage assessment methodology,” in Proceedings of International Workshop on Cryptographic Hardware and Embedded Systems, Saint-Malo, France, pp.495–513, 2015.
|
| [31] |
K. Sakiyama, Y. Li, M. Iwamoto, et al., “Information-theoretic approach to optimal differential fault analysis,” IEEE Transactions on Information Forensics and Security, vol.7, no.1, pp.109–120, 2012. DOI: 10.1109/TIFS.2011.2174984
|
| [1] | XIE Min, TIAN Feng, LI Jiaqi. Differential Fault Attack on GIFT[J]. Chinese Journal of Electronics, 2021, 30(4): 669-675. DOI: 10.1049/cje.2021.05.008 |
| [2] | GAO Si, CHEN Hua, FAN Limin, WU Wenling. Improved Fault Attack on LBlock: Earlier Injection with No Extra Faults[J]. Chinese Journal of Electronics, 2017, 26(4): 754-759. DOI: 10.1049/cje.2017.04.007 |
| [3] | LIU Bozhong, GONG Zheng, QIU Weidong. Automatic Search of Threshold Implementations of 4-Bit S-Boxes Resisting DPA[J]. Chinese Journal of Electronics, 2017, 26(1): 93-100. DOI: 10.1049/cje.2016.10.012 |
| [4] | CAO Yuchen, ZHOU Yongbin, YU Zhenmei. On the Negative Effects of Trend Noise and Its Applications in Side-Channel Cryptanalysis[J]. Chinese Journal of Electronics, 2014, 23(2): 366-370. |
| [5] | SUN Kehui, LIU Xuan, ZHU Congxu. Dynamics of a Strengthened Chaotic System and Its Circuit Implementation[J]. Chinese Journal of Electronics, 2014, 23(2): 353-356. |
| [6] | GUO Zheng, GU Dawu, YUAN Kan, LIU Junrong, HE Yuming. A Novel Method for Power Analysis Based on Combinational Logic in Block Cipher Circuit[J]. Chinese Journal of Electronics, 2014, 23(1): 151-156. |
| [7] | LIU Jiye, ZHOU Yongbin, YANG Shuguo, FENG Dengguo. Generic Side-channel Distinguisher Based on Kolmogorov-Smirnov Test: Explicit Construction and Practical Evaluation[J]. Chinese Journal of Electronics, 2012, 21(3): 547-553. |
| [8] | WU Keke, LI Huiyun, ZHU Dingju, YU Fengqi. Efficient Solution to Secure ECC Against Side-channel Attacks[J]. Chinese Journal of Electronics, 2011, 20(3): 471-475. |
| [9] | MING Yang, WANG Yumin. Identity-based Threshold Decryption Scheme Without Random Oracles[J]. Chinese Journal of Electronics, 2011, 20(2): 323-328. |
| [10] | ZHOU Yongbin, WU Wenling, XU Nannan, FENG Dengguo. Differential Fault Attack on Camellia[J]. Chinese Journal of Electronics, 2009, 18(1): 13-19. |
| Area(kGE) | Latency(clock cycle) | |
| States, keys and constants storage | 4.32 | 0 |
| MixColumns | 3.08 | 0 |
| SubCells | 8.19 | 2 |
| Others | 2.88 | 0 |
| In total | 18.47 | 64 |
| Injection target | Entropy of 16 ciphertext nibbles |
| Input of the last round F (5 exchanges) | 3.878, 3.789, 3.870, 3.857, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0 |
| Input of the last round G (6 exchanges) | 3.951, 3.950, 3.969, 3.962, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0 |
| Input of the penultimate round F (7 exchanges) | 3.992, 3.994, 3.993, 3.994, 3.993, 3.993, 3.993, 3.990, 3.995, 3.992, 3.993, 3.993, 3.993, 3.994, 3.995, 3.992 |
| Input of the penultimate round G (8 exchanges) | 3.999, 3.998, 3.998, 3.998, 3.998, 3.998, 3.998, 3.998, 3.999, 3.998, 3.999, 3.999, 3.998, 3.998, 3.999, 3.998 |